HIPAA is a federal regulatory code system that was put in place to regulate the security, privacy and breach notification rules. These rules were established to help protect the privacy of patients protected health information (PHI).
Description of Security Assessment:
A HIPAA security assessment is the only required regular assessment that must be conducted to meet HIPAA compliance requirements. Security assessments are used to measure the controls in place at an organization and compare them to the requirements of the HIPAA rules. Some of the controls include encryption, access control, data backup, disaster recovery, contingency planning and others.
The HIPAA security rule includes both technical implementation of controls such as password length, encryption of data, and many other controls. The rule also covers the requirements to have policies and procedures in place that identify what the company requirements for compliance are and the process to ensure the requirements are met.
Short description of Privacy and Breach notification Assessment:
The HIPAA privacy assessment can be used, but is not a requirement for compliance, to measure a companies implemented privacy controls (typically policy and procedure based) against the requirements in the HIPAA privacy and breach notification rules. In the Apptega product, the privacy and breach requirements are combined into a single assessment as they are so closely related.
When to use each assessment:
As discussed previously, the only assessment that is required to be conducted regularly is a risk assessment against the HIPAA security rule. To complete the required assessment, the HIPAA security assessment in the Apptega product should be used. If a company also wants to assess against the privacy and breach notification rules, the HIPAA privacy assessment would be used.
HIPAA Security Assessment and Framework v2 (release date December 2, 2024)
The HIPAA Security Assessment and Framework have undergone a full reformat in order to align directly to both the HIPAA Security Rule and the NIST 800-66 guidance. Each control now maps to the requirement in the HIPAA CFR as well as to the guidance on how to implement and assess the control according to NIST 800-66. The new format flows the the controls more easily and provides the HIPAA language as well as the more in-depth NIST guidance for how to interpret the rule. This format will go into production the evening of December 2, 2024.
How the Security assessment is designed to be used:
The Apptega HIPAA security assessment is designed directly off of HIPAA CFR § 164.306, § 164.308, § 164.310, § 164.312, § 164.314, and § 164.316.
Additionally, Apptega uses the NIST SP 800-66 (Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security rule: A Cybersecurity Resource Guide in development of the assessment. This publication was written specifically to help organizations implement and assess against the requirements of the HIPAA Security rule.
The Apptega HIPAA security assessment is set up in a tiered format with the HIPAA rule as the title for the section and the sub-controls located under the HIPAA rule.
Example of a HIPAA rule with one sub-control:
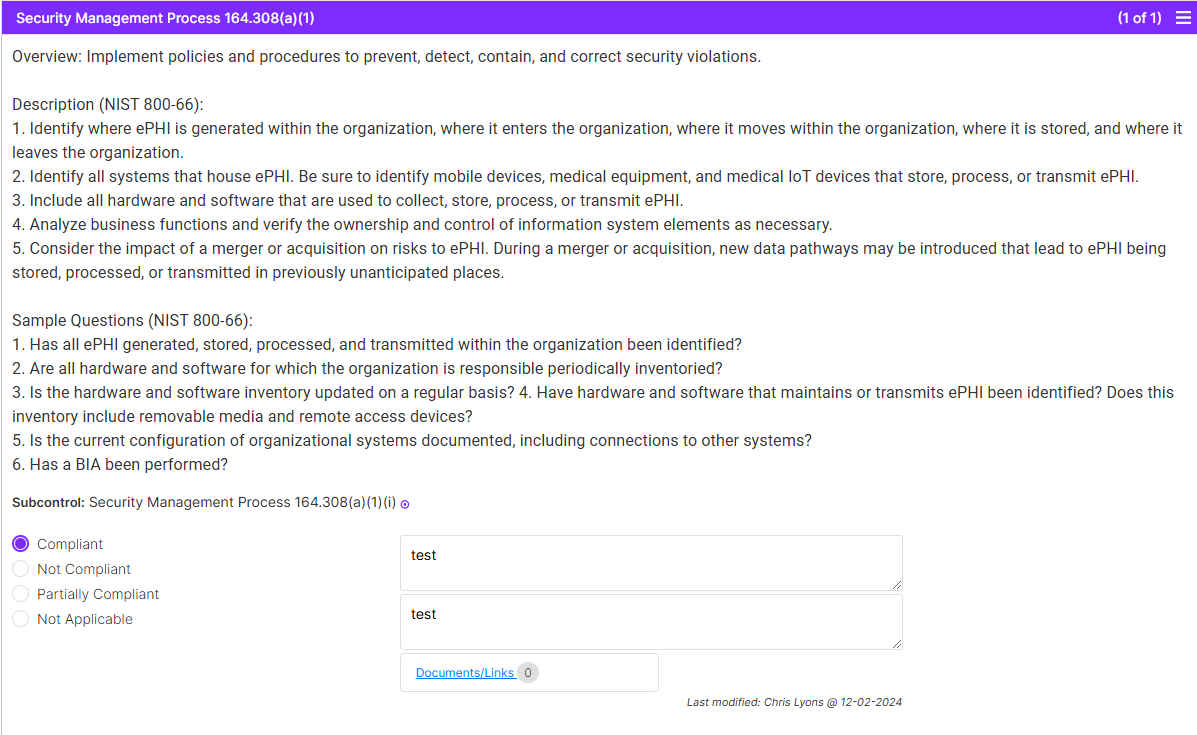
Example of a HIPAA rule with multiple sub-controls:
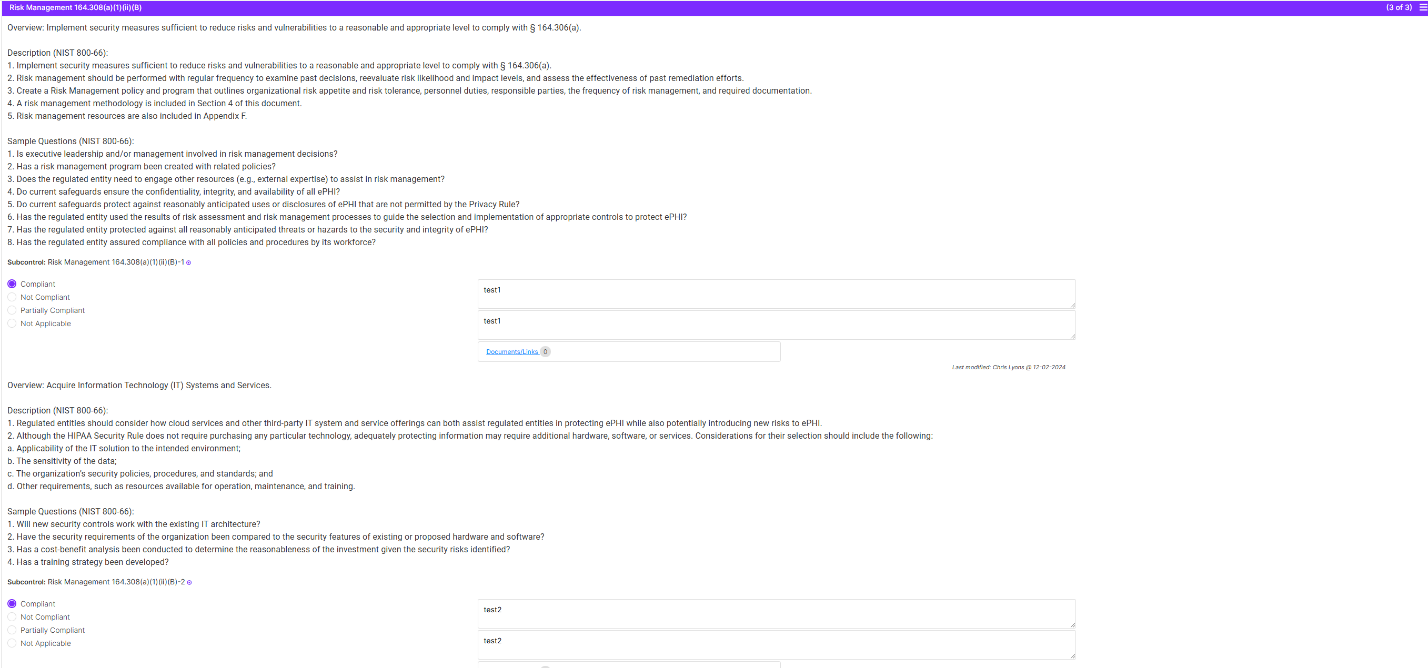
All sub-controls are questions that are directly linked to the requirements in the HIPAA rule with guidance from the NIST 800-66 documentation.
Also note, each control within the HIPAA security assessment has a list of “Sample Questions”. These questions are merely suggested questions that can be asked when conducting an assessment in order to dig deeper into the controls in place to ensure they meet the requirements. All sample questions do not necessarily have to be answered as controls that are in place will vary between entities. Use the sample questions to help guide the process to ensure that all aspects of the organization are reviewed and how they meet or don’t meet the control requirement. The sample questions are provided as part of the NIST 800-66 documentation.
How the privacy/breach notification assessment is designed to be used:
The HIPAA privacy assessment is structured differently than the security assessment due to the way the regulation was written. The HIPAA privacy rule is a set of requirements that are very specific, and many require multiple items within one control to be answered. If one area within the control is not in place, the entire control would not be able to be fully compliant.
Example of a privacy question with multiple requirements:
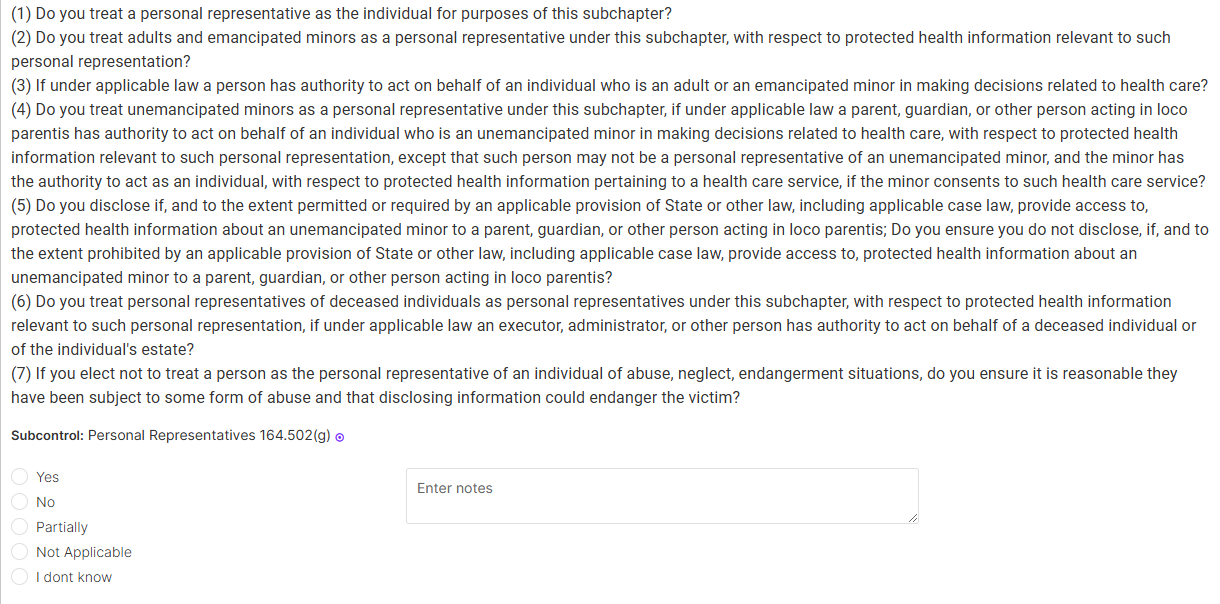
Conclusion:
The HIPAA security rule is much different from the HIPAA privacy and breach notification rules. The HIPAA security rule is written very vaguely to enable organizations of all sizes and business processes to implement the control in a way that makes sense for their organization. The HIPAA privacy and breach notification rules are much more standardized and written to be very specific to the requirements that must be in place in all organizations. The only assessment that is required for compliance is the security assessment. The privacy and breach notification assessments are to help gauge compliance but are not required by the HIPAA regulations.